From privacy payments to privacy collaboration: how passwords reshape the trust and freedom of individuals, business and society
Privacy is never the end. It is the starting point for a freer, fairer and more efficient digital civilization。


This post is co-authored by x TX-SHIELD:

The block chainTransparency is the cornerstone of its trust mechanismBut this..The characteristics of public recordsNow it's beenCore barriers to landing for large-scale applicationsI don't know. For Web3 vision, it's a double-edged sword:It brings verifiable trust at the expense of business secrets, personal wealth privacy and compliance flexibility。
For enterprises, each chain settlement may expose core supplier relationships, procurement costs and remuneration strategies to competitors; for individual users, each chain payment is permanently recorded and made public about their consumption habits, asset status and social relations; and for regulators, a new balance needs to be found between "protection of public privacy" and "performance of financial compliance duties"。
Transparency should not be at the expense of core privacy。It's a common chain(Powered by TX-SHIELD) This marks a new paradigm from an era of "open for trust" to "private trust." This paper will be divided into the following two articles: the previous one will show how privacy payments will address the physical pain of the immediate business, personal and regulatory spheres; the next one will provide you with a picture of the future in which we will look at how we can work together to construct an ecological integrity from the Dark Pool, the secret vote to the secret contest, and the whole new model of social collaboration。
TX-SHIELD is a technology company for the development of privacy payment algorithms. It is a public chain to stabilize currency distributors and DEX to develop a one-stop solution that is regulatoryly friendly and protects privacy. www.tx-shield.com 
Addressing the pain of the moment — the urgent application of privacy payments and the deep analysis
FOR B-END ENTERPRISES: PRIVACY PAYMENTS ARE STRATEGIC INSTRUMENTS FOR BUSINESS COMPETITION AND COMPLIANCE MANAGEMENT
1. Protection of the privacy of pay offers: for example, Deel • Developing “strategic tools” for enterprise talent management
The remuneration system is a core strategic component of the globalized talent competition of modern enterprises, especially multinationals. However, enterprises face a serious problem when they attempt to pay with transparent block chain technology。
A global remuneration management platformDeelFor example, as one of the fastest-growing SaaS companies in history, the core of its business is to deal with employee pay worldwide。Deel actively embraces the block chain technology, which, through its “Deel Cripto” service, allows global employees and contractors to draw on the money instantaneously in encrypted currencies such as Bitcoin and USDC, effectively addressing the pain of slow and costly traditional cross-border wire transfers。However, it is this adoption of efficiency in the payment of block chains that exposes it to serious transparency challenges。
For Deel and the tens of thousands of its clients, if usedOpen and transparent block chainsPaying is done so that each payment chain provides information on the pay structure of the client, the level of pay in different countries and jobs, and even the income of the individual employeePermanent exposureIn public view. This would not only trigger internal pay conflicts and external competitive pitfalls within client companies, but would also reveal directly the core business secrets of the Deel platform, its global payroll database, which poses a fundamental threat to the basis of its billions of dollars valuation。
This current state of affairs, mirrored by the real business landscape, has created a clear and urgent real demand on the part of the enterprise: a globalized enterprise such as Deel, which is already ahead of the block chain of payments efficiency, as well as a large number of companies seeking efficient and transparent pay management, urgently need a payment solution. It has toThe ability to use block chain technology to handle global payroll payments efficiently, accurately and unmovablely, and the absolute guarantee of business confidentiality of remuneration data, as in traditional financial systems, avoid catastrophic data leakage due to transparency of payment instruments。
At present, Web3 and DAO, which are already at the forefront, have successfully tested the feasibility and necessity of privacy payments in pay management through the use of privacy techniques such as Zcash or Aztec Network. These practices have shown that the upgrading of the confidentiality of remuneration from a “contractual commitment” dependent on systems and trust to a “technical assurance” based on cryptography has become a necessary direction for the evolution of management in modern enterprises, particularly in globalized ones。
BenFen Chainwww.benfen.orgThe MPC solution offered by the core engine, TX-SHIELD, is the solution tailored to meet the needs of such enterprises. We further suggested that a complete enterprise-level privacy payroll enterprise could pay its global workforce through a chain that would complete the entire process, ensuring the accuracy and auditability of the payment process and concealing key information such as the amount paid, the identity of the issuer and the recipient. For an enterprise, the system will serve as a “hidden strategic asset” to support efficient and transparent global salary management while comprehensively safeguarding the enterprise's core pay data and business strategies; for a block chain ecology, the system is expected to be a key step in promoting large-scale landings at the enterprise level — It accurately responds to the core concerns of enterprises such as Deel in the highly sensitive chain of pay management, clearing critical barriers to the integration of block chain technology into mainstream business applications。
Supply chain finance and settlement: for example, apples and Fuscon break the twin dilemma of “data isolation” and “extra-transparent”
The current financial dilemma in the supply chain is rooted in the inability to communicate trust efficiently among participants. An in-depth analysis of the McKinsey Global Payments Report indicates that global supply chain finance has a financing gap of as much as trillions of dollars a year. The essence of this gap is a classic “trust” issue. The business data between Apple and its core supplier, Fuscon, for example, form a typical “data island”. This makes it difficult for the financial institutions to prove themselves innocent of the “receivables” that represent the real context of the transaction, and ultimately leads to a difficult and expensive financing of the entire chain. However, simple adoption of block chains in the pursuit of data sharing and transparency would be a more deadly dilemma: the most central commercial secrets, such as the precise purchase unit price of apples for Fuscon, the settlement period between the parties and the scale of production of new products, would be exposed to all participants in the chain, including competitors. Competing parties can use this precision to calculate the cost structure and product strategy of apples, a new risk introduced by the resolution of old problems, which greatly hampers the location of block chain technology in the core business landscape of enterprises。
The complex industrial chain, represented by the automobile industry, the consumer electronics industry and its vast network of suppliers, is seeking an innovative solution that simultaneously meets two seemingly contradictory objectives: first, the automation of business processes and the validation of key data, the need for trust and the removal of financing bottlenecks; and, second, the need to ensure that all sensitive business details are absolutely protected during the collaborative process to avoid the leakage of core competitive advantages。
Intra-industry exploration has demonstrated the feasibility of this direction. The Baseline Protocol project (co-sponsored by major players such as Ernst and Young, Microsoft and AMD) was a pioneer in this area. At its core is the use of advanced cryptographic techniques to enable enterprise systems to synchronize business processes along publicly owned block chains while ensuring the confidentiality of all commercially sensitive data. This practice strongly demonstrates that it is possible to achieve “competition in synergy” through technical means — that is, to build a strong data moat for each participant while enhancing overall efficiency and trust in the supply chain。
THE PRIVACY PAYMENT FUNCTION OF THE CHAIN WAS BORN IN RESPONSE TO THIS COMPLEX CHALLENGE. BASED ON THE PROVEN PRIVACY TECHNIQUES OF TX-SHIELD, WE CAN BUILD A CREDIBLE SETTLEMENT LAYER ON THE BLOCK CHAIN. AT THIS LEVEL, SUPPLIERS CAN DEMONSTRATE TO FINANCIAL INSTITUTIONS THE VALIDITY AND COMPLIANCE OF THEIR RECEIVABLES WITHOUT DISCLOSING ANY SENSITIVE INFORMATION RELATING TO SPECIFIC AMOUNTS, THE IDENTITY OF THE COUNTERPARTY OR THE CONTRACT PARTICULARS. THIS PROVIDES FINANCIAL INSTITUTIONS WITH KEY CONFIDENCE ELEMENTS FOR THEIR DECISION-MAKING WITHOUT DISCLOSING ANY COMMERCIAL SECRETS. REFERRING TO MCKENZIE ' S PROJECTIONS OF DIGITAL SUPPLY CHAINS, SUCH PROGRAMMES ARE EXPECTED TO SIGNIFICANTLY OPTIMIZE SUPPLY CHAIN LIQUIDITY EFFICIENCY, REDUCE THE SETTLEMENT CYCLE FROM MONTHS TO DAYS, AND PROVIDE A POWERFUL NEXT-GENERATION INFRASTRUCTURE TO ACTIVATE THE INDUSTRIAL CHAIN AND REDUCE THE COST OF INTEGRATED FINANCING。
3. CROSS-BORDER B2B PAYMENTS AND SETTLEMENTS: BALANCING EFFICIENCY, COST AND COMMERCIAL CONFIDENTIALITY, FOR EXAMPLE, WITH SHEIN GLOBAL SUPPLY CHAIN
Traditional cross-border payment systems have been limited to speed and cost issues for decades. Payments through traditional agency channels, such as SWIFT, usually take two to five days to complete, and are accompanied by high fees and non-transparent middle ground. In the case of Shein, the global fast-fashion giant, the business model is highly dependent on a global supply chain network of thousands of suppliers requiring rapid response. It is therefore extremely sensitive to the efficiency and cost of cross-border payments. To address the ills of the traditional SWIFT system, industry naturally explores more efficient block-chain programmes such as the stabilization of currency. However, even if new instruments, such as the introduction of a currency of stability, seek to improve efficiency, enterprises still have to face the confluence of data privacy rules (e.g. EU GDPR) and complex compliance requirements between different jurisdictions. Moreover, for SHEIN, each payment in the transparency block chain may inadvertently reveal to its competitors, Temu, its precise purchase price for different suppliers, its order allocation strategy and even its global allocation path, which poses a direct threat to its core barriers to competition. Enterprises urgently need a payment solution, which must be accompanied by privacy guarantees for the traditional banking system, stable currency settlement speed and compliance flexibility to cope with complex global regulatory frameworks。
BenFen Chain Privacy Payment provides an entirely new solution for this, a “B2B cross-border privacy settlement layer”. The programme uses TX-SHIELD ' s privacy protection and currency stabilization technology, whereby cross-border transactions between enterprises can be completed almost instantaneously in the chain, while key transaction amounts and counterparty identification information are hidden and visible only to both parties and authorized regulatory bodies. The expected effect of the programme is to achieve a second-rate settlement that reduces average handling costs by more than 50 per cent and, in the process, ensures that core business secrets, such as procurement strategies and distribution channels, are not leaked, thereby creating a critical information advantage for enterprises in a fierce global trade competition。
4. Privacy of treasury management: re-engineering of the enterprise block chain financial system using the example of MicroStrategy
In the process of accelerating the digitalization of the global business communityTreasury ManagementFrom back-office functions to one of the core business strategies. It not only determines the security and liquidity of enterprise funds, but also directly affects capital structures, market signals and strategic decision-making. However, as more and more enterprises try to optimize the treasury structure using block chains and encrypted assets, new problems also emerge — while efficiency increasesTransparency of information presents a risk of strategic exposureI don't know. American listed companiesMicroStrategyFor example, this enterprise is the world's most famous “head of the block chain bank”. Since 2020, MicroStrategy has continuously purchased bitcoin with its own funds through bond financing and its incorporation into enterprise balance sheets to counter inflation and optimize long-term value reserves. While this has become a milestone in the innovation of asset allocation for enterprises, it has also exposed the privacy of the open books of the block chains. Every time a company carries out a transfer of funds, rebalancing of assets or a new round of purchases, it is recorded and analysed in real time in the chain, and any market observer can speculate on its position, cost zone or even future operational intent from the course of the transaction. This means that, while providing transparency and trust, the block chain exposes the financial movement of enterprises, the investment tempo and even the internal financial structure to global analysts. For a listed company, not only can market volatility and speculation be triggered, but it can also affect firm market value management, bond ratings and even precision control of capital market signals。
More and more enterprises are not content with the closure and slowness of traditional treasury systems, and are also beginning to explore the real-time financial system of chained blocks, but are they equally concerned — is it equal to all financial flows when public books are introduced? Therefore, there is an urgent need for an enterprise to achieve both the “immediate settlement and automated movement” advantages of the block chainProtection of the privacy of funds and compliance with audit requirements, as in traditional banking systemsThe treasury program。
ExactlyPrivate payment systems in the chainIT'S A UNIQUE VALUE. THE COMPLEX MPC TECHNOLOGY PROVIDED THROUGH TX-SHIELD ALLOWS ENTERPRISES TO ENCRYPT KEY FINANCIAL INFORMATION (INCLUDING TRANSACTION AMOUNTS, FLOW, ASSET STRUCTURE) WHILE COMPLETING THE TRANSFER OF ASSETS, REINVESTMENT OF PROCEEDS, OR STABILIZATION OF CURRENCY MOVEMENTS. THE SYSTEM AUTOMATICALLY GENERATES VERIFIABLE ENCRYPTION CERTIFICATES, WHICH ARE ACCESSIBLE ONLY TO AUTHORIZED AUDIT BODIES OR REGULATORY NODES. IN THIS WAY, THE ENTERPRISE IS ABLE TO OPERATE THE TREASURY EFFICIENTLY WITH A BLOCK CHAIN AND TO ACHIEVE “UNVISIBLE” PRIVACY PROTECTION IN THE CONTEXT OF THE CHAIN。
If MicroStrategy operates the treasury management under this structure, its movements of funds, currency distribution and asset rebalancing will no longer be exposed to the open market, but will nevertheless ensure that all chain operations are in compliance with the regulations, auditable and consistent with financial reporting. In other words, it enables enterprises to achieve the true meaning of “encrypted verifiable treasury”: public regulation, private execution。

DAO Treasury Management and Anonymous Financing: Building a “strategic barrier” to decentralised organizations, using the example of Uniswap DAO
Large DAOs (e.g. Uniswap DAO) usually manage hundreds of millions or even billions of dollars of assets, and the full transparency of their treasury, while a cornerstone of community governance, brings with it real realities and pains: when Uniswap DAO considers investing in an early DeFi project, full-public details of negotiations and transfers can easily capture other giant whales or competitors, leading to a surge in buy-in costs for DAOs and a complete failure of investment strategies. A strong practical need is to provide a degree of operational privacy for teams or specific committees in implementing investments, grants and rewards for contributors, while maintaining effective community oversight of the overall health status of the treasury and the overall direction of its use, in order to protect its competitive strategy and operational efficiency。
We envisage the provision of a dedicated “bank privacy” module for DAO on this sub-chain. & nbsp; DAO can make specific confidential investments through the privacy payments function of the chain, anonymous funding of projects, and private incentives for contributors. After the event, DAO can demonstrate to the community, through selective disclosure mechanisms, the overall reasonableness and compliance of the use of funds over a specific period of time, without having to disclose the details of each sensitive transaction. The technical feasibility of this solution has been tested in its official usage by the private sector block chain projects such as Aztec Network. In addition, the Messari report Understanding Decentralised Secret Calculations (DCC) provides an industry perspective and provides a theoretical framework for such explorations to introduce data confidentiality capabilities while maintaining decentrization. This programme will empower DAOs to acquire “business secrets” protection capabilities similar to those of traditional companies, thereby attracting more traditional capital and institutions seeking strategic privacy to the Web3 world through the DAO model, promoting further prosperity and maturity of decentrized ecology。
FOR END-USER C: PRIVATE PAYMENT IS A TECHNOLOGICAL FOUNDATION FOR PERSONAL FINANCIAL DIGNITY AND FREEDOM OF LIFE
Protection of daily consumption and digital life: protecting “digital personality” in the case of encrypted money traders
As the global infrastructure for encrypted monetary payments improves — from encryption cards from Visa, Mastercard, to mainstream financial technology companies like PayPal, Revolut and others that integrate USDC payments — an increasing number of users are beginning to use encrypted money to complete their daily transactions in the real world. The block chain payments are moving from “integrity of investors” to “the way of life for the general public”. However, one neglected fact is that:The full transparency of the open chain is making “digital life” a glass house that can be seen。
It is envisaged that a well-known encrypted money dealer or Web3 entrepreneur, if all his consumer behaviour — from buying Starbucks coffee, paying Netflix subscriptions, to buying holiday gifts for his family — is paid through the same public wallet, can be easily traced, aggregated and analysed. Zone chain analysis companies, advertisers, etc. can thus outline his life trajectory, wealth distribution, preferences, and even health and family ties. Such transparent data exposure threatens the privacy, security and even personal freedom of individuals. In fact, this is not an individual case. According to the 2024 annual reports of Chainalysis and CipherTraceMore than 70 per cent of the chain of identification is created by the behaviour of users exposed in “day-to-day transactions” rather than in large-scale investment activities。CoinDesk and The Block also stated in their comments: “Without privacy, the payment of encrypted currency will remain at the experimental stage forever.”
In order for Web3 payments to become truly mainstream, it is important not only to address “efficiency and cost” issues, but also to allow users to regain “the privacy boundaries of digital personality”. In other wordsPrivacy is a prerequisite for paying for the move towards popularization, not a technical option that adds value。
BenFen Chain's privacy payment system was designed for this core pain point. Based on the chainBenPay (www.benpay.com)Ecology, where users can use BenPay eco-applications - BenPayCard to complete daily small payments such as meals, subscriptions, travels, online consumption, etc., to enable stable currency payments to be integrated into daily daily small payments in a lower threshold and higher frequency, such as catering, subscription, travel, online consumption, etc. The system is based on complex MPC technology and automatically hides the amount, time, recipient information of each transaction and the relevance of the address between the different transactions. At the same time, the sub-chain also designed a "selective disclosure mechanism" - – Users can give limited transaction visibility to commercial or regulatory agencies when needed to achieve “verifiable but not tracked” payment experiences。
The intended effect of this programme is not only to guarantee personal privacy, but also to facilitate the movement of block chain payments towards real social universality:
• for ordinary consumers, it means restoring cash-like freedom in the digital world — consumption is no longer an entry point for data mining
• for businesses, it enhances user confidence and promotes the use of a higher frequency Web3 primary payment
• & nbsp; for regulatory purposes, privacy is no longer the equivalent of a “black box”, but rather a “boundary transparency”。
In the longer term, it’s not the samePrivacy payments will be the lowest public facility for digital lifeI don't know. It is both a technical expression of the sovereignty of personal data and a prerequisite for a truly socially integrated Web3 economy。

2. Protection of the purchase of sensitive goods and services: for example, the purchase of prescription drugs to safeguard the privacy of individual consumption
In the context of increasing concentration of global compliance pressures and payment platforms, consumers are gradually losing their last line of defence for privacy protection when purchasing legitimate but sensitive goods or services. Traditional payment systems, through centralized accounts and identification mechanisms, allow each transaction to be traced and analysed, which is tantamount to exposing personal life to spotlights for groups requiring regular purchases of prescription drugs or mental health services。
The rise of block chain payments, particularly stabilization currency payments, offers a completely new possibility for such scenarios: It hasImmediate settlement, cross-border accessibility, non-intermediated freezing riskSuch advantages are particularly suited to sensitive consumption scenarios in internationalized digital life. However, the nature of this transparent book also raises more difficult questions - when a transaction involving the purchase of medicines or psychological counselling is recorded in the chain, anyone can trace the act of buying it, thus restoring the health, state of life and economic condition of the individual. This “transparent inverse” makes block chain payments less available in areas where privacy is most needed。
Mainstream media such as CoinDesk have commented on several occasions that “without privacy, encrypted currency payments will be difficult to adopt in mainstream consumption scenarios”. This judgement is well established in the market — the use of private currencies such as Monero in some of the electrical and sensitive services sectors is indicative of the rigid demand of users for privacy protection. However, such programmes often conflict with compliance requirements and have difficulty accessing mainstream payment systems。
BenFen ChainThe privacy payment function is very useful for such scenarios. Users can make payments to businesses through BenPay ' s eco-application, the entire process is completed along the chain to ensure the execution of the transaction, but key transaction amounts, information on the parties ' addresses and the specific consumption content derived from it are hidden. This allows users to safely access the services they need without fear that the core details of private life will be permanently recorded in public books and become a future hazard. We want to further promote privacy payments as “a default payment option for sensitive consumption scenarios”. For users, it is like providing a “consumer freedom amplifier” to safeguard their fundamental right to consume on the basis of individual will, without harm to others, and to defend their dignity; it is a crucial step for the ecologicalization of block chain payments to meet the deep needs of users in mainstream consumer markets, as it addresses a reality point that also exists in traditional electronic payments, but is greatly magnified on the block chain。
Protection of freelancers and microbusinesses: using the example of Upwork designers, individual “business secrets protection”
Today, when the global digital economy and remote collaboration flourished, the demand for efficiency and flexibility in cross-border settlements by freelancers and microbusinesses increased rapidly. An increasing number of people are introducing block chains and stable currency payments as new options for cross-border collection and settlement. Whether they are creative people working on traditional platforms such as Upwork, Fiverr, or Web3 developers serving DAO, NFT, they are increasingly accepting stable currency payments such as USDT, USDC, etc. The reasons are realistic: block chains pay for cross-border accessibility, instant settlement, lower transaction costs and circumvent the complex processes and geographical constraints of traditional banks. This makes stable currency a new common currency for the global free-trade market。
However, as more individual economic activities go up, they are also passively exposed to “full transparency” books. A top-level UI designer, who is on the Upwork list, may serve both financially strained start-ups and the world ' s top 500 customers, whose pricing strategies, income fluctuations and even major client sources can be easily detected by competitors, customers and even third-party data analysis firms once they are all on the chain. This state of “naked-link” makes her passive in price negotiations and may even cause problems of trust and dispute, directly undermining her commercial pricing capacity and market competitiveness. Individual operators also need to protect their “business secrets” — especially pricing strategies and customer relationships. In traditional economies, such information is naturally protected by the privacy and commercial confidentiality of bank accounts, but in the chain economy they are virtually without barriers。
This phenomenon of “transparent reversal” is becoming a concern for a new generation of individual economies. While centralized payment platforms such as Stripe and Payoneer provide some privacy protection, users are required to place data fully on the platform and cannot control their own business information. As CoinDesk also pointed out in his 2024 report“In the Web3 economy, privacy is no longer a personal issue, but part of the competitiveness of the business.”The underlying chain of privacy payments is the structural solution provided for such user groups. By using the chain of payments, individual workers and businesses can safely complete payments along the chain, while hiding the amount of the transaction, the identity of the counterparty and the relevance of the transaction, thereby effectively preventing external inferences to their offer strategy or customer relationship. The mechanism preserves the efficient, low-cost and global advantages of block chain payments, while providing similar confidentiality to traditional business systems, allowing individual economic participants to have for the first time a “technical-level bargaining umbrella”. Allow independent designers, developers, content creators and cross-border traders to control their own business data security, as large enterprises do, in a fair and respectful market environment。
Financial self-defence in geopolitics: building an “economic lifeline” using Turkish designers as an example
At a time when geopolitical and macroeconomic risks are intertwined, the block chains are gradually becoming a “financial self-defence tool” for some parts of the population. In countries such as Turkey and Argentina that have experienced hyperinflation or strict capital controls, freelancers, small business owners and even ordinary depositors are often unable to secure wealth or cross-border payments through traditional banking systems. As a result, they began to shift to block chains and stable currencies, and digital assets became “alternative lifelines” against devaluation and capital blockades。
But a new dilemma emerged: the openness and transparency of the block chains made them “naked” on the chains. To take the example of a Turkish resident, if he wished to convert part of his income into a dollar-stable currency in order to resist the lira’s devaluation, he found that all transfers, asset balances and conversion paths were exposed to the chain, meaning that all his financial footprints could be exposed to public view. This puts them at double risk: on the basis of these public records, regulators may determine that their actions are contrary to capital flow policies, thereby initiating a process of “freezing first, then vetting”, which leads to asset locking; at the same time, open wealth makes them extremely vulnerable to unlawful targeting. This “vulnerability of transparency” has significantly reduced the protective role of the block chain in high-risk countries。
This is creating a strong real need: people need not only decentrized value storage tools, but even more, in areas where capital is limited and currency is volatilePrivacy protection mechanisms— A financial infrastructure that can “live” in an environment of mistrust. The payment of privacy in the chain is a response to this. When users save on the chain and transfer points through the BenPay C2C completion point, the balance of their assets and information on their counterparties will be hidden, so that they can use stable currencies to resist inflation and avoid the risks associated with transparency in the chain. The urgency of this trend is also confirmed by research data from Chainalysis, which show a significant increase in the use of encrypted currency retail in areas of high inflation and political instability. We believe that privacy payments are not just a technological innovation, but a “financial human rights” infrastructure. It provides a last line of defence for individuals in need to protect their wealth and free trade, and serves as an “economic escape module” for them to sustain economic activity and protect their dignity in extreme circumstances。
5. Safeguarding the Pureness of Charitable Donations: for example, by using anonymity as a good example, to protect the heart of good
In the field of charity, public figures, entrepreneurs or ordinary persons of good will often face pressure from public opinion, moral kidnapping or continuous requests for donations once the donation is made public, after having made donations in large or sensitive areas. For example, an entrepreneur who wishes to finance cutting-edge technological exploration or marginal artistic creation may not wish his name to be publicly associated with the donation in order to avoid unnecessary business attention or public misunderstanding. This has changed the taste of what should have been pure good deeds, even for some potential donors. Individuals who wish to do good deeds anonymously, as well as charities that focus on the protection of donor privacy, need both a way of ensuring that good money reaches recipients safely and retroactively, and a way of fully protecting donor anonymity so that goodwill can flow freely. The case of Vitalik Buterin, the founder of the Taifeng factory, who used Tornado Cash to make anonymous donations to Ukraine is a strong example of a strong desire to protect donor privacy even for industry leaders in certain circumstances。
BenFen Chain's private payment is the ideal tool for achieving this goal. Donors can contribute directly through the chain to the public address of the charity, completely concealing the donor ' s wallet address and the specific amount of the donation. It could further promote the establishment of “philanthropy privacy payments” standards in cooperation with large public benefit foundations. Reshaping the culture of charity and encouraging more self-inflicted donations, in particular by involving donors who are unwilling to be rich or, for various reasons, wish to remain low-key in the public good, so that good deeds truly return to their purest and most liberal nature。
& nbsp; for G-end and third parties: Privacy payments are the next generation of regulatory technologies to achieve “precision compliance”
Achieving “auditable privacy”: exploring a new paradigm for AML/CFT compliance, for example, with the Tornado Cash incident
The traditional financial regulatory system is under unprecedented pressure as the technology of block chains evolves, especially with increased anonymity and privacy protection. Regulators have traditionally relied onRetroactivity of transactionsandSubject identifierWHILE THE TWO PILLARS CARRY OUT THE AML/CFT FUNCTION, STRONG PRIVACY TECHNIQUES, WHILE PROTECTING USER DATA, ALSO REDUCE THE ABILITY OF REGULATORS TO ACCESS TRANSACTIONAL INFORMATION ON THE CHAIN. SUCH “TECHNICAL BLINDNESS” HAS FORCED REGULATORS TO RELY ON TRADITIONAL MEANS SUCH AS TERRITORIAL JURISDICTION, SANCTIONING CONTROLLED ENTITIES AND FAILING TO DISTINGUISH BETWEEN LEGITIMATE USERS AND VIOLATORS, LEADING TO REGULATORY MEASURES OFTEN BEING CHARACTERIZED AS “ONE-SIZE-FITS-ALL” — BOTH AGAINST ILLEGAL ACTIVITIES AND RESTRICTING CITIZENS' FREEDOM TO ENGAGE IN LEGITIMATE PRIVATE TRANSACTIONS。
Tornado Cash is a typical example of this dilemma. In 2022, the United States Department of the Treasury sanctioned Tornado Cash for the use of the Mixer for money-laundering, including money flows related to the Korean hacker organizations (U.S. Treasury, 2022). Incidents have shown that in cases where anonymous transactions cannot be managed efficiently, surveillance can only be conducted by indirect means to control risks and cannot accurately identify legal and irregular transactions. This reveals a deep contradiction: privacy techniques designed to protect individual rights and a regulatory system to protect public safety are caught up in the current architecture. Regulators urgently need a technical tool to enable them toNon-monitoring of all legal transactions and non-violation of public privacyIn this context, effective and accurate identification and control of illegal activities, i.e., a leap from “black blockade” to “precision governance”。
IN THIS CONTEXT, IT PROPOSES INNOVATIVE SOLUTIONS FOR “AUDITABLE PRIVACY”. THROUGH COMPLEX MULTI-PARTY SECURITY CALCULATIONS (MPCS), WE PLACE COMPLIANCE CAPACITY AT THE LEVEL OF AGREEMENT, MAKING “REGULATORY” A CENTRAL FEATURE RATHER THAN AN AFTER-ACTION FUNCTION. IN PARTICULAR, REGULATORS CAN VERIFY THE COMPLIANCE OF TRANSACTIONS (E.G. “THE TRANSACTION DOES NOT INVOLVE AN ADDRESS ON THE SANCTIONS LIST”) WITHOUT HAVING TO LOOK AT THE AMOUNT OF THE TRANSACTION AND THE IDENTITY OF THE PARTICIPANTS, THEREBY UPGRADING THE TECHNICAL PARADIGM FROM TRADITIONAL “DATA REGULATION” TO “LOGICAL REGULATION”。
The structure of the chain is adoptedDouble layer compliance design:
•FIRST TIER: THE BASIS OF THE KYC IDENTITY
IN COOPERATION WITH THE COMPLIANCE SERVICE PROVIDER, PROVIDE THE ENTERPRISE AND HIGH FREQUENCY USERS WITH A CHAIN-BASED KYC CERTIFICATION AND GENERATE VERIFIABLE CERTIFICATES. THIS NOT ONLY ENSURES THE LEGITIMACY OF THE PARTICIPANTS, BUT ALSO PROVIDES THE INSTITUTIONAL BASIS FOR AML/CFT, WHICH SERVES AS AN ANCHOR OF TRUST FOR ALL HIGH-LEVEL FINANCIAL ACTIVITIES, PARTICULARLY CORPORATE PAYMENTS, PAYROLL, ETC。
•Second level: auditable privacy at the protocol level
BASED ON IDENTIFICATION COMPLIANCE, THE MPC IS COMBINED WITH ZERO-KNOWLEDGE PROOF TECHNOLOGY TO ACHIEVE PRIVACY PROTECTION AND AUDITABILITY OF TRANSACTIONS. REGULATORS CAN VERIFY COMPLIANCE WITHOUT DISCLOSING THE AMOUNT OF THE TRANSACTION OR THE IDENTITY INFORMATION OF THE PARTIES, THEREBY GUARANTEEING TACIT PRIVACY TO THE VAST MAJORITY OF LEGITIMATE TRANSACTIONS, WHILE PROVIDING PRECISION GOVERNANCE TOOLS FOR REGULATION。
This two-tiered structure systematically addresses the core regulatory contradictions: regulators can effectively combat illegal activities and businesses and individual users can protect financial data and business secrets under compliance frameworks. As a result, the sub-chain provides a critical infrastructure for large-scale enterprise-level applications of block-chain finance, deconstructing privacy and compliance and ushering in a new era of compliance technology。
2. Improving the efficiency of tax audits: building more harmonious relationships with small and medium-sized technology firms, for example
In traditional tax audits, tax authorities usually require enterprises to provide several years of bank flow and account details to verify the accuracy and compliance of their tax declarations. In the case of a medium-sized technology company, it is required not only to provide a book of transactions for the past few years, but also to face the problem of auditing processes that take months and seriously disrupt the R & D and operational tempo. More importantly, company management has been concerned that core business secrets, such as customer lists, partners and pricing strategies, may be leaked during lengthy audit processes. This model reflects the dilemma common to both sides: to ensure tax equity while minimizing disruption to the normal operations of enterprises。
As block chain technology matures, enterprises begin to explore the use of block chain to record transactional data in day-to-day operations to enhance efficiency, transparency and security. Some block-link platforms (e.g., the Taifung, Hyperledger) allow real-time chaining and automated recording of financial transactions, potentially facilitating tax audits. PricewaterhouseCoopers (PwC) has also proposed options to use block-chain technology to track corporate taxes and transactions with a view to improving tax compliance and transparency and reducing the burden of manual auditing through chain data。
However, major problems remain in the existing block chain programme: while transparent books provide complete records of transactions, the amount of each transaction, the parties to the transaction and their connections are made public, which can lead to the disclosure of business secrets of enterprises, particularly sensitive data relating to customer lists, revenue structures and partner information. Thus, traditional block chain records alone do not address the need for enterprise privacy protection in the audit process。
BenFen Chain ' s privacy payments and related technology were developed to fill this gap. When an enterprise uses its own chain to record transactions in its day-to-day operations, it can produce the necessary proof during the audit process to verify the proposition with the Tax Administration without disclosing the details of each transaction. This “data availability” design, while ensuring audit compliance, effectively protects business confidentiality and client privacy of enterprises. Further, the chain integrates complex privacy computing techniques (complex MPCs) into the protocol layer and combines the certification of the KYC under the chain to form a "two layer compliance system " . Regulators can verify the compliance of transactions without having to look at specific amounts and information on both parties to the transaction to achieve the high standards of “default privacy, selective disclosure”. This not only increases the efficiency of tax audits and reduces the cost of corporate compliance, but also helps to build more trust and efficient cash relations and promotes large-scale application of block chains in the areas of corporate financial management and tax compliance。
The 12 scenes that we have examined in depth, together confirm a core view: privacy payments are not a marginal function, but rather a core component of repairing the critical flaws of the existing block chain paradigm and unleashing its real potential. It allows block chain technology to better serve the mainstream business community, individual users and regulatory systems by providing sophisticated technical safeguards for business confidentiality, personal dignity and compliance efficiency。
However, this is only the beginning. When “pay privacy” becomes a reliable foundational capability, a broader space for innovation will be opened. Imagine:
• & nbsp; how many times will DeFi ' s liquidity increase if the agency can implement a strategy on the chain without being targeted?
• How fair can governance be if DAO votes are no longer influenced by large households?(e.g. A16Z has a veto in Uniswap)
• how accurate will the price be found if the competition is no longer expected to be anchored by the first bid?
• how many new modes of collaboration can emerge if enterprises can jointly analyse data without revealing business secrets?
These scenes were unattainable in the past, not because they were technocratic, but because the contradiction between transparency and privacy was not resolved。When you have to choose between "open exchange of trust" and "privileged but isolated", many high-value collaborations can never happen. Now let's think furtherWhat can we build with privacy when it becomes infrastructure, not luxury goods?
It's not a technical showdown, it's a redefinition of trust -- from "open trust" to "encrypted trust" and "transparent collaboration" to "in privacy."。
Building the dream of the future -- from "private payment" to "private collaboration": a paradigm leap
Over the past decade, we have witnessed a breakthrough in privacy technology in the area of payments -- agreements like Zcash, Monero, Tornado Cash that make it untraceable who turns who to whom? This is the 1.0 age of privacy technology:Can not open messageI don't know。
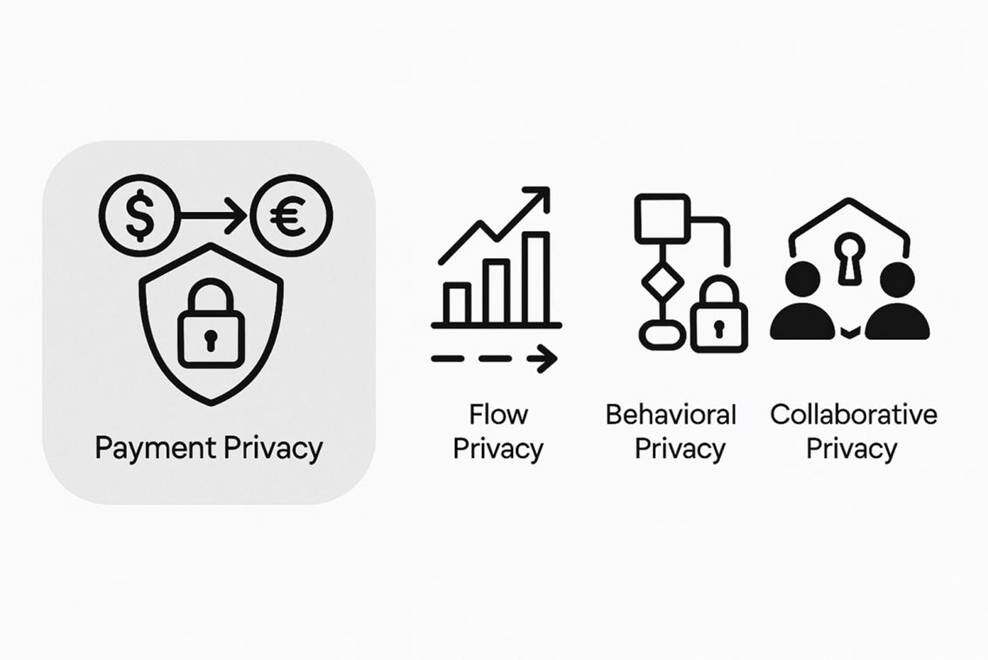
But paying for privacy is just the beginning. The real future lies in:Process privacy(Flow Privacy)Behavioural privacy(Behavioral Privacy) and eventuallyCollaborative privacy(Collaborative Privacy)。
What's the difference between these three?
• & nbsp; Process privacy: Hide trading strategies, market behaviour and intent patterns
• & nbsp; Behavioural privacy– Hide transactions, strategic paths and market intentions to prevent speculation of operating patterns
• & nbsp; Collaborative privacy: creation of "protected spaces for collaboration" between parties, absence of local data, insight sharing in secret
We are confident that the future world will focus on "protected collaboration", redefining the boundaries of payment, trade, governance and social cooperation。
Privacy is no longer invisible. It is "selectedly seen."。
Trust no longer originates from the centre, but rather from verifiable encryption collaboration。
This is not a minor technical patch, but a rebuilding of the trust infrastructure。
1. & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; transactional privacy: the birth of Dark Pool on the chain
Why do institutions need privacy markets?
The transparency of traditional block chains is protective of the diaspora and a curse on institutions。
When a regulatory agency carries out large transactions along the chain, the whole market sees: the counterparties can speculate about your strategy, the arbitragers can rob your order, the competitors can reset your model. This "coercive transparency" fills the chain with information asymmetries and distorts the price discovery mechanism。
In traditional finance, Dark Pool exists precisely to address this problem — allowing large transactions to take place anonymously and avoid market shocks. But the central Dark Pool has fatal defects:
• & nbsp; The operator can do evil: Robbing transactions, leaking information, fixing prices
• & nbsp; Non-transparent regulation: Unable to verify whether the transaction is fairly executed
• & nbsp; Single-point risk: The collapse of a centralized system will destroy the entire market
TX-SHIELD IS BUILDING, ONERegulatory private market level(Regulad Dark Pool On-Chain) — a trading infrastructure that achieves “selective transparency” in a decentralised environment. It is this infrastructure that is pictified and the core carrier。
How does technology make "selective and transparent"?
The central challenge here is:How can the parties see each other and the regulators intervene if necessary, but leave the rest of the market players unknown?
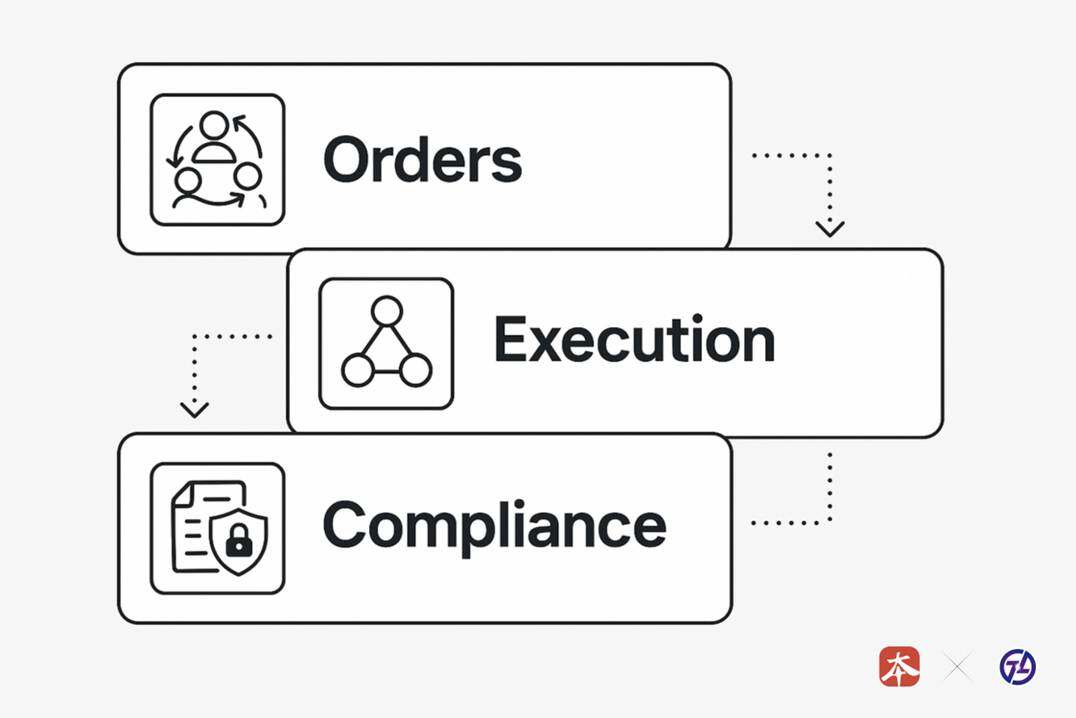
TX-SHIELD USES A MULTILAYERED PRIVACY STRUCTURE:
1. & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp;Order Layer: ORDER MATCHING MECHANISM BASED ON MULTIPLE SECURITY CALCULATIONS (MPCS), TRANSACTIONAL INTENT TO SUBMIT AND BROKER IN SECRET
2. & nbsp; ; Executive Level: ZKP ENSURES THAT THE VALIDITY OF THE TRANSACTION IS VALIDATED, BUT THAT THE SPECIFIC PARAMETERS (PRICE, QUANTITY, IDENTITY) ARE NOT DISCLOSED
3. Compliance Level: Selective disclosure mechanism (Secretative Disclosure), with a decryption key held by the regulator and access to a particular transaction record under judicial proceedings
This means:
• & nbsp; The market is no longer manipulated by the public- the intention to keep the transaction confidential before execution
• & nbsp; Institutions can implement strategies safely on the chain- Don't worry about the leak
• & nbsp; STABLE COINS, RWAS CAN CIRCULATE IN PRIVACY- Compliance and privacy
Dark Pool is not just a market toolThe bottom base of private financeI don't know. It allows traditional financial institutions, for the first time, to give serious consideration to "uplinking", as they no longer need to choose between transparency and tactical protection。
2. & nbsp; DAO Governance: How to Reshape DAO
DAO GOVERNANCE DILEMMA: THE COST OF TRANSPARENCY
THE IDEA OF MOVING TO CENTRAL SELF-GOVERNMENT ORGANIZATIONS (DAO) IS TO ALLOW COMMUNITY MEMBERS TO MAKE DECISIONS BY VOTING TOGETHER, REPLACING TRADITIONAL HIERARCHICAL STRUCTURES WITH CODES AND CONSENSUS。
BUT IN REALITY, DAO GOVERNANCE IS OFTEN COUNTERPRODUCTIVE:
• & nbsp; The results were observed in advance: Large-house voting will influence decision-making in small households, with a wind effect
• & nbsp; Social influence kidnaps reason: THE WELL-KNOWN PUBLIC POSITION OF KOL WILL SUPPRESS DISSENT
• & nbsp; Bribery and collusion: When the results are visible in real time, coordination of the attack becomes easier
The root causes of these problems are:Excessive transparency leads to information asymmetries rather than addressing them。
True democracy requires two conditions: freedom of expression (without any influence from others) and verifiable results (ensure that there is no cheating). The traditional public vote met only the second condition。
Secrecy voting: restoring integrity in governance
TX-SHIELD'S SECRET VOTING MECHANISM BASED ONSame encryption(Homomorphic Encryption) andMultiple security calculations(MPC):
• ballot papers submitted by voters are submitted in a confidential state to the chain
• the counting process is carried out in encryption and no one can see the content of a single ballot
• the final result is certified publicly through zero knowledge to ensure that the counting process is correct
THIS SEEMS SIMPLE, BUT THE DAO LOGIC OF TRUST HAS BEEN REDEFINED:
"Intimateness makes governance honest. "
Within this framework:
• & nbsp; ; ; ; the vote is independent of each person and is not influenced by others
• & nbsp; ; large households are unable to manipulate small households through "sign display"
• the validity of the result can be mathematically validated rather than relying on trust
More importantly, this mechanism could extend toMore complex governance scenarios:
• & nbsp; Graded governance: voters with different weights, the weights aggregate in a secret state
• & nbsp; Commissioning votes: the trust relationship is confidential, but the vote is retroactive
• & nbsp; Projected market: Decentralized forecast market based on secret ballot
WHEN GOVERNANCE MOVES FROM "OPEN TRANSPARENCY" TO "VERIFIABLE PRIVACY", DAO REALLY HAS THE POTENTIAL TO BECOME A NEW FORM OF ORGANIZATION。
3. the true value of confidential competitive release
What is the nature of the competition?
In economics, competition is seen as a "price discovery mechanism" — a competitive return of goods to real value。
But there is a fundamental flaw in traditional competition:Information anchor effect(Anchoring effect)。
When the first bidder bid 1 million, the psychological expectations of others are anchored near that figure. Even if people think it's worth 2 million, he could just bid 1.1 million -- because he's stupid because he's afraid of being too high。
The result is:The competition is not finding prices, but is guiding them。The first bidder controls the psychological expectations of the entire market。
Seal the race chain
TX-SHIELD'S PRIVACY COMPETITION MECHANISMSealed bidding(Sealed-Bid Action):
1. & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp;Submission phase: No one (including the auctioneer) can see the exact amount of the bid submitted by the bidder for encryption
2. & nbsp; ; Discovery phase: All bids are automatically decrypted by smart contract after the agreed time
3. Settlement phase: the highest bidder wins, the others return their bids (or a second-price auction is designed under the mechanism)
"It's the first time that the market has actually made it."Competition for information symmetry" - Each bidder's bid is based on its own true valuation and not on the signals of others。
APPLICATION SCENARIO: FROM NFT TO CARBON CREDIT
This mechanism can be applied to all scenarios that require "fair price discovery":
• & nbsp; NFT AUCTION: The value of art is determined by real needs, not expectations
• & nbsp; Carbon credit market: Enterprise bidding based on actual abatement costs rather than strategic bids
• & nbsp; Spectrum auction: Government sells spectrum resources and operators cannot press down prices through signal games
• & nbsp; Data auction: Company competition for data sets under privacy protection to avoid price leakage of business strategy
Secrecy contests are not only a technical tool, but also a critical step for privacy technology to enter the value discovery layer。It proves that privacy is not an enemy of efficiency, but a prerequisite for a fair market。
4. & nbsp; unlocking completely new modes of collaboration
The end of privacy: the reshaping of social collaboration
If the first three scenarios are the application of privacy technology at the level of "transaction" and "governance", the fourth dimension is:Reconstructing social collaboration itselfI don't know。
When individuals, institutions, machines can work together safely in a state of secrecy, we begin to unlock new socio-economic models — models that were not possible in the past because of the “high cost of trust” or “no privacy”。
Scenario one: an anonymous creative reward system
ProblemThe authors often face "identity bias" when they publish their work: the work of well-known authors is subject to easy attention and new ones are buried. This led to a distortion of the evaluation system。
TX-SHIELDProgramme:
• the work is encrypted as it is submitted
• ; & & nbsp; & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & & nbsp; & & & & & & & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & ; & & & & & & & & & nbsp; & & nbsp; & &
• & nbsp; ; the creator may choose public identity when the quality of the work reaches the threshold
• & ; & & ; & & & & ; & & & & ; & & & ; & & & & ; & & & & & ; & & & & & & & ; & & & & & & & & ; & & & & & & & & & & & & & & & , & & & nbsp; & & & nbsp; & & & ; & & & & & & & & & & & & nbsp; & & &
This model has demonstrated its potential in the fields of music, literature, design — when "work" and "author" are untied, the value of creativity is simply assessed。
Scenario two: going to centralized credit lending
ProblemTraditional credit assessment relies on centralized institutions (banks, letters of credit companies), but they either fail to cover users worldwide or there are data monopolies and privacy abuses。
TX-SHIELD PROGRAMME:
• user chain behaviour (trading history, DeFi participation, social reputation) is codled into "credit rating" under a secret state
•
• scoring model administered by community, with transparent algorithms but data privacy
It's an "encrypted data to assess credit, not identity" modelPopulation without bank accountsUnbanked also has access to financial services while protecting privacy from abuse。
Scenario III: Inter-enterprise joint data collaboration
ProblemTHERE IS A LARGE AMOUNT OF HIGH-VALUE DATA AVAILABLE IN HEALTH, FINANCE, LOGISTICS, ETC., WHICH CANNOT BE SHARED DUE TO PRIVACY REGULATIONS (GDPR, HIPCA) AND COMPETITIVE RELATIONSHIPS. THIS HAS LED TO THE RESTRICTION OF AI MODEL TRAINING AND THE INSIGHT OF INDUSTRY。
TX-SHIELD PROGRAMME:
• & nbsp; based onFederal studies(Federated Learning) andMULTIPLE SECURITY CALCULATIONS (MPC)Frame, data left at enterprise level
• model training is conducted in a confidential state and only gradient updates are shared (and gradients are treated with differential privacy)
• the final model is owned by all participants, but none of them has access to the original data of the other party
This model is changing areas such as medical research (Multi-Hospital Joint Training Diagnostic Model), financial controls (MBI anti-fraud) and supply chain optimization (MME-predicted demand)。
THIS IS THE VISION OF THE MPC-FL FRAMEWORK OF TX-SHIELD: A SYSTEM THAT MAKES PRIVACY AN INFRASTRUCTURE FOR SOCIAL COLLABORATION. MORE CRITICALLY, TX-SHIELD ADDRESSES THE CENTRAL CHALLENGE OF FEDERAL LEARNING: HOW CAN EACH PARTY'S CONTRIBUTION BE QUANTIFIED FAIRLY? THIS IS THE ESSENCE OF TX-SHIELD AND TRADITIONAL FEDERAL LEARNING PROGRAMS。
In traditional federal learning, all participants together train a model, but it is not possible to measure exactly who has contributed much. This leads to two fatal problems:
• & nbsp; A hitchhiking problem:The poor-quality side of the data has the same rights
• & nbsp; Incentive imbalance:The high-value party has no incentive to remain engaged
THE TX-SHIELD FRAMEWORK IS CALCULATED IN A CONFIDENTIAL MANNER, SO THAT WITHOUT EXPOSING RAW DATA,Quantification and scoring of each party ' s model contribution:
• & nbsp; ENTERPRISE A CONTRIBUTED 30%- The marginal contribution of its data to the accuracy of the model
• & nbsp; ENTERPRISE B CONTRIBUTED 34%- The data cover the key long end scene
• & nbsp; ENTERPRISE C CONTRIBUTED 36%- It's of the highest quality and lowers the model
Based on this contribution measure, benefits are automatically allocated:
• & nbsp; Governance: Voting weights are proportional to contributions, and high contributors have greater voice in model iterative decision-making
• & nbsp; Right to proceeds: Model commercialization revenues are distributed by contribution, with more effort
• & nbsp; Data sovereignty: any party may withdraw at any time and its contribution is recorded but data is not retained
This contribution is not a one-time calculation but is updated as the model evolves。When a party provides high-quality data on a continuous basis, its share of equity increases gradually; if the quality of data declines or stops contributing, the share decreases accordingly. Only when the model is no longer updated will the distribution of entitlements be consolidated。This creates an incentive for self-improvement— Participants have the incentive to provide high-quality data on a continuous basis rather than "a hammer for sale"。
THIS IS THE ESSENCE OF TX-SHIELD AND TRADITIONAL FEDERAL LEARNING PROGRAMS。
Google's Federate Learning and OpenMined solutions the question of "how to train under privacy" but they acquiesce in the equality of all participants — whether you provide 1 million high-quality data or 10,000 noise data, you have the same interest。
TX-SHIELD FURTHER ANSWERED:How can fairness of collaboration be ensured under privacy protection?We not only protect privacy, but also quantify contributions and distribute entitlements。
This "verifiable fairness" changes collaboration from "moral restraint" to "institutional security":
In the field of health care, there is a level playing field between the large Sanctuary Hospital and the primary clinic, which provides data on complex cases, and the primary clinic, which provides data on common diseases, both of which are accurately measured and no longer "big hospital-led, small clinic-run"。
In the area of finance, large banks and small financial technology companies can combine to counter fraud — the historical data of large banks and real-time data of small companies are of value, and equity is distributed on the basis of actual contributions, and is no longer a zero-sum game。
In the supply chain area, branders, logistics companies and retailers can jointly optimize inventories - each party's data (sales forecasts, transport efficiency, stock turnover) are quantified as concrete contributions to model improvements and the benefits are shared proportionately。
This is not just technological innovation, but a revolution in the paradigm of collaboration: when contributions can be quantified, trust can be counted; when rights are validated, collaboration can occur and continue。
scenario iv: & nbsp; csi and quantification of data
The most radical images are:THE FUTURE INTELLIGENCE IS NOT A SINGLE AI BUT AN AI NETWORK。Several AIAgents will collaborate in the trusted privacy layer, like neurons that make up the brain -- individual neurons that are ordinary, network connections that create consciousness。
WHY DOES AI NEED TO COLLABORATE?
TODAY'S AI MODEL IS BECOMING MORE SPECIALIZED: SOME ARE GOOD AT IMAGE RECOGNITION, SOME ARE GOOD AT NATURAL LANGUAGE, AND SOME ARE SPECIALIZED IN MATHEMATICAL REASONING. HOWEVER, PROBLEMS IN THE REAL WORLD OFTEN REQUIRE CROSS-CUTTING CAPABILITIES — THE DIAGNOSIS OF DISEASES REQUIRES ANALYSIS OF MEDICAL IMAGES, MEDICAL HISTORY TEXTS AND GENETIC DATA AT THE SAME TIME; AUTOMATIC DRIVING REQUIRES INTEGRATION OF VISUAL PERCEPTION, PATH PLANNING AND TRAFFIC FORECASTING。
A SINGLE AI CAN'T DO EVERYTHING, AND COLLABORATION IS INEVITABLE。
BUT HERE'S THE FUNDAMENTAL PARADOX: THE AI MODEL IS ASSET, COMPETITIVE. WHEN TWO AIS NEED TO WORK TOGETHER, THEY CAN'T SIMPLY "PUBLICLY" EACH OTHER... THIS COULD LEAD TO REVERSE ENGINEERING OF MODELS, EXTRAPOLATION OF TRAINING DATA AND DISCLOSURE OF COMMERCIAL SECRETS。
THE CORE TX-SHIELD PROGRAM IS TO PROVIDE A PASSWORD INFRASTRUCTURE TO BUILD AI COLLABORATION。
Specific scene:
Medical diagnostic collaboration
• Agent A (Image AI) analyzed the CT scan and found lung anomalies
• &Agent B (pathological AI) infers the probable cause of the disease based on the description of the symptoms
• &Agent C (genetic AI) patient-based genotype assessment treatment
• & ; and three AIs exchange reasoning under a confidential state to generate a comprehensive diagnostic report
• & nbsp; but no AI can see other AI model parameters or training data
Financial wind control collaboration
• &Agent A (trade AI) detection of unusual transaction patterns
• & nbsp; &Agent B (Credit AI) assesses the historical credit records of users
• &Agent C (anti-fraud AI) cross-check multi-source data
• ; final output risk rating, but models and data for AI remain isolated
Autopilot collaboration
• & Vehicle AI needs to collaborate with the urban transportation system AI, Weather Forecast AI, Logistics Movement AI
• they share the necessary information (road, weather, distribution needs) in a confidential state
• ; but each of their algorithmic logic, historical trajectories, business strategy remains private
Technical realization: confidential model reasoning collaboration
WHEN AI INTELLIGENTS NEED TO SHARE MODELS, EXPERIENCES, REASONING RESULTS, THEY SHOULD NOT EXPOSE DATA DIRECTLY TO EACH OTHER (WHICH COULD LEAD TO REVERSE ENGINEERING OR DATA LEAKAGE) BUT SHOULD EXCHANGE INFORMATION IN A CONFIDENTIAL MANNER:
• & nbsp; & Agent A and Agent B jointly deduce a conclusion without exposing their respective models
• & & Agent C can verify the validity of this conclusion but cannot reverse model parameters for A and B
• the collaboration process can be audited but the reasoning details remain private
THIS "SECRET COLLABORATION" WILL BE THE FOUNDATION OF THE FUTURE AI ECONOMY。
When AI Agent starts owning assets (encrypted wallets, digital identities), performing contracts (linked smart contracts), providing services (API calls, data exchange), the trust between them must be at the level of code -- not "I believe you don't do evil," but "ciphery assures you can't do evil."。
FURTHER, THE TX-SHIELD CONTRIBUTION QUANTIFICATION MECHANISM COULD ALSO BE APPLIED TO AI COLLABORATION:Each Agent ' s contribution to the final result can be quantified and the proceeds distributed proportionately。THIS MAKES IT A REAL "ECONOMIC COLLABORATION" BETWEEN AI, NOT JUST A TECHNICAL INTERFACE。
Imagine a future Web3 collaboration based on the TX-SHIELD framework:
• a medical diagnostic mission completed by five professional AI collaborations at $100
• & nbsp; & nbsp; 35% video AI contribution, 30% pathological AI contribution, 20% genetic AI contribution, 10% pharmaceutical AI contribution, 5% coordination AI contribution
• & nbsp; and automatic distribution of proceeds: $35/30/20/10/5
• the entire process is verifiable on the chain, but each AI model and data is fully private
IT'S NOT SCIENCE FICTION, IT'S CODE SCIENCE, BLOCK CHAINS, AI INTEGRATION。
TX-SHIELD wants to be the trust infrastructure for this AI collaborative network -- to make Agenic AI or robots work as humans, but more credible than humans. In the new paradigm, trust comes from cryptography — you don't have to disclose information, you just have to prove that you followed the rules。Zero knowledge certification, multi-party security calculations, federal learningThese technologies make "validation" and "public" untie and "collaboration" separate from "exposure"。We believe that privacy is not a border, but a bridge to the future。
Conclusion: Privacy is the new language of trust
Starting from “resolving the pain of the moment”, we have witnessed how privacy payments serve as a strong shield to protect business secrets, safeguard personal dignity and achieve precision compliance. It has repaired the inherent flaws in the chain of transparent blocks, making it truly capable of serving the real world. In turn, we are moving towards “the dream of building the future”, thinking of the infinite possibilities that arise when privacy becomes a default setting. From the chain of Dark Pool to the secret ballot, from the secret race to the brand-new paradigm of data collaboration, it is clear to us that privacy is no longer just about “hidden”, more about “enabling”; it is not just a shield for defense, but an engine for collaboration。
This is a profound paradigm shift: we are moving from an era in which “transparency for trust” is necessary to a new era in which “ciphery guarantees trust”. The source of trust shifted from forced public exposure to verifiable confidential calculations。
THIS IS THE VISION OF THE JOINT EXPLORATION OF THE PUBLIC CHAIN WITH TX-SHIELD: WE ARE NOT ONLY DEVELOPING A FUNCTION OR A SET OF PROTOCOLS, BUT ALSO BUILDING THE TRUST BUILDING BLOCKS OF THE NEXT GENERATION OF INTERNET. IN THIS FUTURE:
Enterprises can work together without fear in competition to stimulate innovation
Individuals can live freely in the digital world and regain sovereignty
Society can achieve more efficient collaboration and unleash collective wisdom while protecting privacy。
Privacy is never the end. It is the starting point for a freer, fairer and more efficient digital civilization. And we are working together to make it a reality。
AboutBenFen
BenFen is a high performance public chain specifically designed to stabilize currency payments. We have built a secure, low-cost and highly scalable bottom-up network based on the Move language. Its core feature is supporting users to pay the Gas fee directly in stable currency, which significantly reduces the threshold for use and paves the way for large-scale applications. On the basis of its strong cross-chain and multi-currency clearing capacity, the chain covers multiple payment scenarios through rich ecological applications. More importantly, we provide enterprise-level users with critical privacy payment options to ensure that they benefit from block chain efficiency advantages while protecting core business data from disclosure。
It is dedicated to becoming a global network of stable currency flows for service enterprises that pay, cross-border payments, electricians and offline traders, a next generation of financial infrastructure that combines efficiency, cost and safety。
AboutTX-SHIELD
TX-SHIELD IS A REGULATORY CHAIN PRIVACY INFRASTRUCTURE THAT PROVIDES BOTH PARTIES WITH PRIVACY AND A VISUAL PAYMENT AND SETTLEMENT CAPABILITY FOR THE APPLICATION OF THE STABLE CURRENCY AND BLOCK CHAIN。
Core solutions:
• & nbsp;TX-SHIELD:Privacy infrastructure for block chain applications to achieve confidential transactions, Dark Pools and privacy-centred protocols。
Our innovation:
WE NOT ONLY PROTECT THE PRIVACY OF TRANSACTIONS, BUT ALSO RECREATE THE TENURE AND SECURITY OF ASSETS THROUGH DISTRIBUTED PASSWORDS. THE TX-SHIELD PROGRAMME ENABLES BUSINESSES AND FINANCIAL INSTITUTIONS TO CO-HOST ASSETS, PRIVATE LIQUIDATION AND REGULATED COMPLIANCE AUDITS WITHOUT DISCLOSING BUSINESS SECRETS。
We are building an infrastructure like this:Let privacy no longer become an obstacle to regulatory and institutional adoption, but rather a shield for financial flows。
TX-SHILD-- The price and regular treatment base-player for stalablecoin, blockchain and enterprise.