CEO, WHICH ACCOUNT WAS STOLEN, REVEALING THE KEY SECURITY RISKS BEHIND MONETIZATION
The blacking and triggering of the modulus boom in the bank's executive Yi He social account reveals the systemic dangers of the encryption industry at three levels: “weak social access, weak currency structure, and insufficient user risk awareness”. 。

On December 10th, 2025, several encrypted media reports reported that the micro-credit account of the Co-Foundation CEO, Yi He, had been hacked in a short period of time and that during the control period it had sent to its contact an emulsion called MUBARA (Mubarakah). Subsequently, the currency experienced an abnormal increase in a short period of time and was accompanied by sharp fluctuations. The events generated widespread concern, not only because of the involvement of money executives, but also because of the prism, reflecting the multiple deep-seated problems of social account security in the current market, monetization mechanisms and user risk perceptions。
This paper will seek to penetrate the surface and dig into the bottom logic, based on publicly available media coverage and retrogressive data on the four dimensions of facts, mechanisms, risks and industry impacts。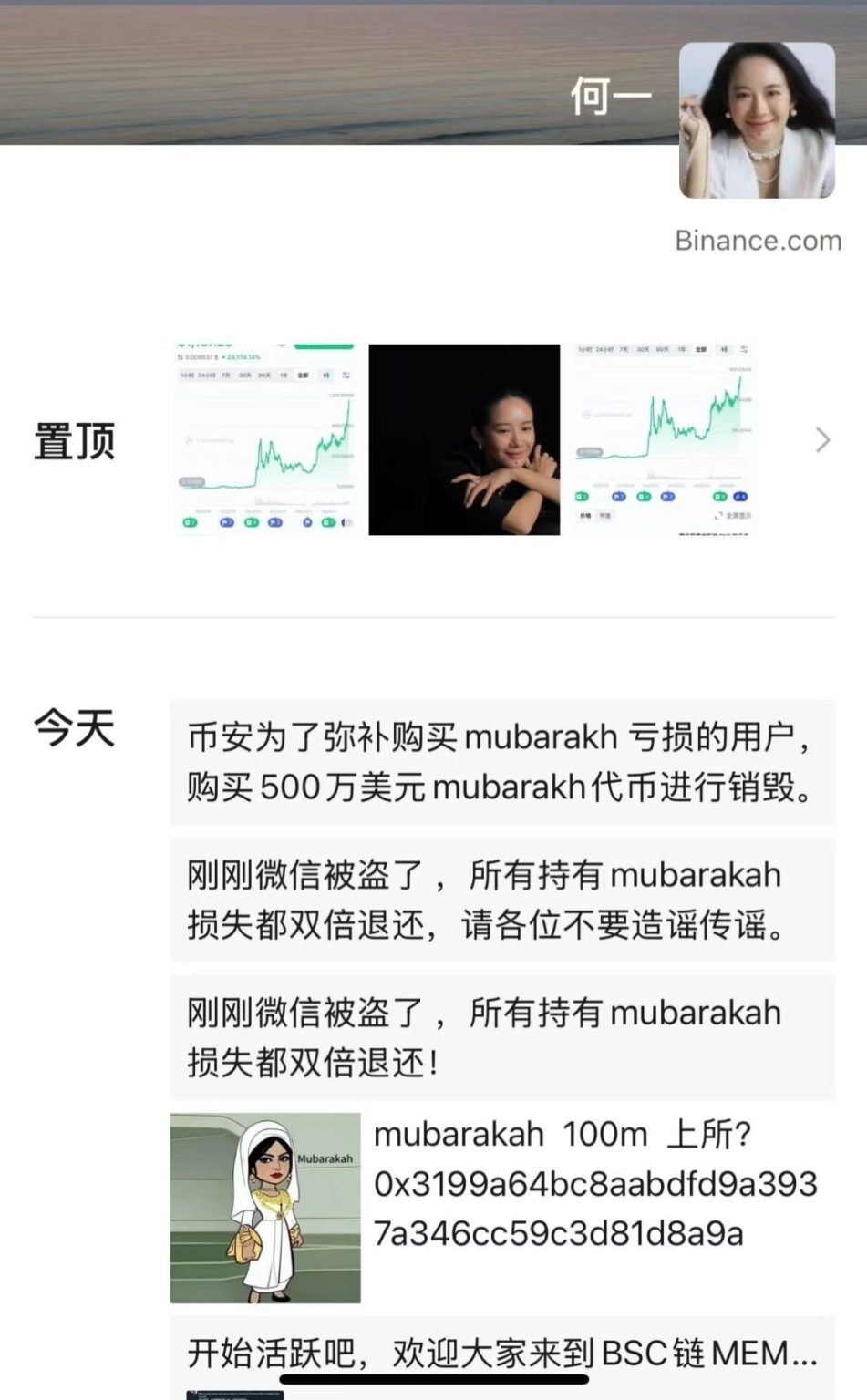
Review of events: from stolen accounts to currency fluctuations
According to authoritative media disclosures and chain data tracking by CoinDesk, Criptopolitan, CriptoNews and others, the event process is broadly as follows:
(i) Social accounts hacked
The micro-intelligence account was temporarily controlled. The hackers use their micro-intelligence to send contact persons promotional information related to the MUBA. It is worth noting that the credibility of the account numbers of Web2 as the mainstream social platform of the Web2 era continues to have a strong influence within the encryption industry, particularly in terms of the importance of trust in private communications and the flow of industry information, which has set the stage for subsequent market reactions。
(ii) Evidence of early layout of data along the chain
SEVERAL ANALYSTS NOTED THAT TWO NEW WALLETS PURCHASED APPROXIMATELY US$ 19 MILLION IN MUBAA HOURS BEFORE THE ROLL-OUT. THE CURRENCY HAS SINCE RISEN RAPIDLY, AT ONCE BY MORE THAN 200 PER CENT, AND THERE HAVE BEEN SIGNIFICANT SALES AT A HIGH LEVEL, WITH SOME GAINS EXCEEDING $40,000. THE CHAIN BEHAVIOUR CLEARLY SHOWS THE TYPICAL COMPLETE STRUCTURE OF THE "EARLY BUILDUP INFORMATION TRIGGERS PULL UP AND DROP."。
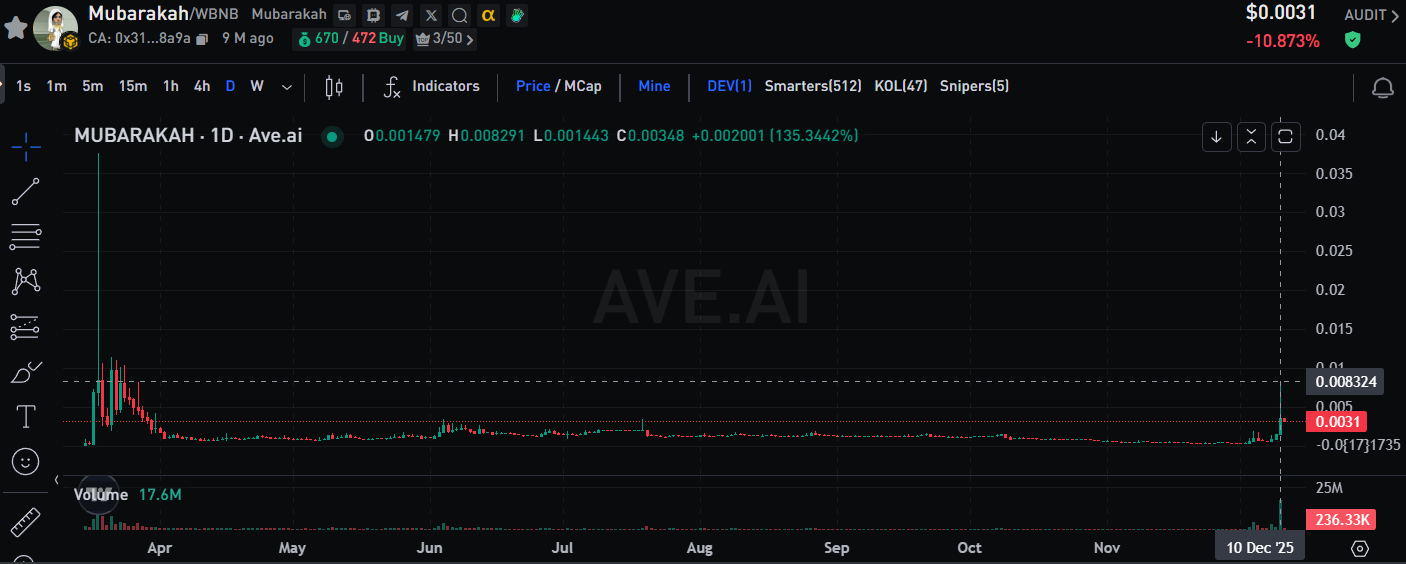
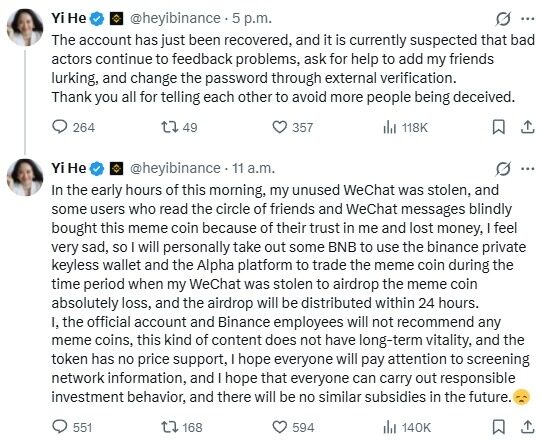
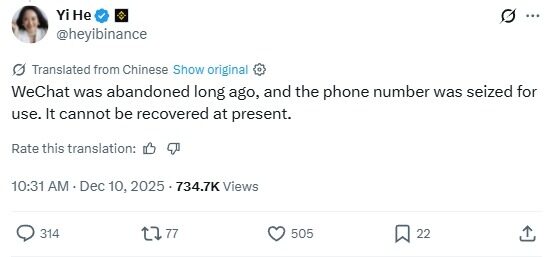
(III) OFFICIAL AND CZ RESPONSES
Zhao Chang Peng (CZ) warned users at the first time on the social platform not to believe in token recommendations from stolen accounts and highlighted the significant security risks to social accounts on the Web2 platform. The Team subsequently confirmed that the account numbers had been recovered and that the simultaneous issuance of security alerts to the fraud had not been further expanded。
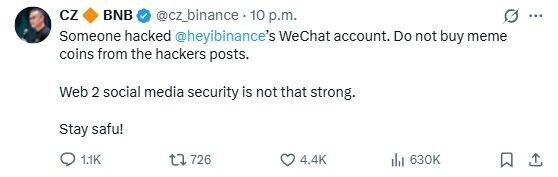
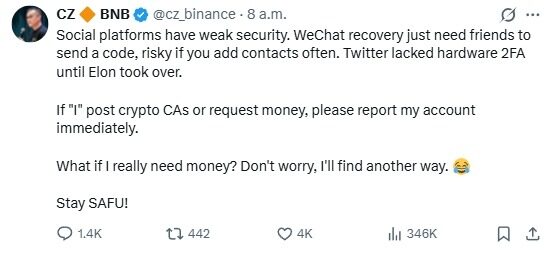
Cross-cutting mechanisms along the chain with social dimensions: a typical “trust hijacking” incident
Structurally, this is not a mere hacking event, but rather the result of a multiplicity of mechanisms。
(i) Social identity hijacking is less expensive than asset hijacking
As the social platform is hosted by Web2, its security depends on the platform ' s internal mechanisms. Trust within the encryption industry is very personal (e.g. founders, CEOs, early investors, etc.), which means that hackers need only a short time to control a high-trust account to trigger real market behaviour. This “information entry” type of risk is becoming a general industry safety grid。
(ii) Increased impact of attacks due to low liquidity and high volatility
Modular currencies often have the following characteristics: low market value and extremely low operating costs; investor sentiment as the dominant price; heavy reliance on external narratives and direction; and lack of foundational judgement. Once there is a “similar endorsement” incentive, even information published by stolen accounts is sufficient to trigger rapid price fluctuations. This structure of the monetary market provides a natural amplifier for such events。
(iii) A closed chain of trust in the path of event information dissemination
We believe that the environment of the private sphere has a strong channel of trust: the source of information = the executive of the industry, the channel of information = the communication of the private domain, the form of information = the direct forwarding, the private exchange, the information validation threshold = the very low. In this environment, it is easy for some users to accept “internal information”-type hints, so that transactions can be followed up quickly。
III. Structural risk exposure in the encryption industry
The event itself had been contained, but it revealed systemic problems in the industry that merited further discussion。
(i) Social account security has become a new face of attack on Web3
With the development of the industry, the social accounts of projecters, exchange executives and KOL have become the main portal for Web3 information dissemination. These entry points are more vulnerable than smart contract or exchange security systems: Web2 platform relies on traditional security mechanisms such as account codes, text-message authentication; lack of chain-based identification; and non-molecularity. Thus, such “account hijackings and market fluctuations” are almost inevitable in the future。
(ii) The speed at which information is disseminated and the speed at which it is reacted leads to end risks
The encryption market is still highly information-asymmetrical: hackers or manipulators occupy the upper end of the information chain, the general user is located at the tail, and the market response mechanisms are similar to “conductive” rather than “balanced”. As a result, a small number of people have less time to access information than to create a quick profit window。
(iii) Natural lack of risk pricing capacity for monetized currencies
Value analysis based on fundamentals is virtually non-existent in the monetized currency market, based only on emotions, social signals, information stimuli and celebrity effects. This means that, as long as narratives are briefly hijacked, prices deviate from normal. Such incidents are not uncommon, but are a corollary of the structural weaknesses of the monetized market。
IV. User-level risks: Why is it that investors are eventually harvested
While the incident was caused by hacking, it was the user who bore the real risk。
(i) Users often make decisions on the basis of “known identities”
Many do not judge on the basis of token structure, mobility, contractual security, but rather on the basis of which information comes from, “know-how”, what appears to be an internal opportunity and time-bound pressure. This logic of judgement is easily exploited by the attackers。
(ii) Lack of information validation mechanisms
Many users have failed to do so: second confirmation of origin, checking with official channels, checking the mobility of the chain, analysing the size of the pool and identifying “early build-up” behaviour. This risk is further amplified in the young and speculative ecology of the Model participants。
(iii) Spreading is always the slowest reaction
A standard time difference chain is used by a chauffeur who buys hackers and promotes the use of coins to spread into the game. It is difficult to avoid being in the last part of the chain and eventually becoming the bearer of the loss。
V. Industry revelations: How to reduce similar incidents in the future
From an industry perspective, the event provided at least three important insights:
(i) Official announcement channels with verifiable links between the projecter and the transaction
For example, the DID (de-centre identity) binding, chain signature bulletins, de-centre identity certification, multi-platform synchronized updating mechanism. Through such mechanisms, user reliance on a single Web2 platform is reduced and information credibility is enhanced from the source。
(ii) Social account security should be part of industry-level risk management
This includes, but is not limited to, stronger validation of executive social accounts, establishment of a multi-level internal validation mechanism by teams, and social access segregation management for key personnel. The cost of such safety protection is much lower than the cost of a single market fluctuations。
(iii) User education must be upgraded
Educating users: do not rely on “know-how”, do not judge authenticity on a single screenshot, do not pick up low mobility coins, and do not equate monetary coins with “internal opportunity”. Only when user perceptions are upgraded will the scope of such frauds really decrease。
Concluding remarks
The fact that the blacking of a micro-intelligence account has largely subsided, without causing large-scale losses, cannot be ignored: the trust structure of the encryption industry is being further amplified by “social access” and “monetization”. An information source from stolen accounts can trigger price volatility, suggesting that industry remains highly dependent on sources of information, and the characteristics of the monetized currency market further exacerbate the vulnerability of such reliance。
In the long term, the industry needs systematic improvements in identity mechanisms, information validation mechanisms, user education and social portal security. Specifically, there is a need for a three-fold upgrading: a shift from “personal trust” to “credible identity on the chain”; a shift from “Web2 one-way transmission” to “validable release on the chain” in the information mechanism; and a shift from “blindness and wind” to “reasonable decision-making” in the user perception. Otherwise, similar events will be repeated, and the real damage will remain with ordinary investors。